
tashatuvango - Fotolia
How to ensure cybersecurity and business continuity plans align
We're diving into how and why organizations should have a collection of emergency-focused plans in place that can interact with each other if a cybersecurity attack occurs.
Cybersecurity attacks are often business-affecting events that should trigger business continuity and disaster recovery plans. Is that true in your organization?
News reports on ransomware attacks, distributed denial-of-service (DDOS) attacks, phishing and virus attacks occur on a regular basis. Fortune 500 organizations, such as Facebook with 540 million affected records and Capital One Bank with 80,000 affected bank accounts and 140,000 Social Security numbers, have sustained significant losses and damage to their reputations from these cyber incidents. And threats of attacks from well-known cybersecurity threat actors such as Russia, China and Iran pose an ongoing threat to many U.S. organizations.
Assuming IT leaders are being proactive to protect sensitive data by initiating security policy and measures to identify and isolate potential cybersecurity attacks -- i.e., firewalls and intrusion detection systems/prevention systems (IDS/IPS) -- they might consider the organization well-protected with proper cybersecurity plans and security standards in place.
But how would an organization handle a cybersecurity attack that neutralizes critical network resources, servers, databases, applications and desktop devices? Do the cybersecurity plans -- if they're in place -- link to additional critical emergency plans, specifically business continuity (BC) and disaster recovery (DR) plans?
Here, we'll examine linkages that need to exist among cybersecurity and business continuity plans, the role of incident response (IR) plans, as well as provide guidance on ensuring that an organization's cybersecurity and BC/DR plans are synchronized so they can collectively mitigate the potential severity of a cyber event or security breach to the business.
Is information security enough?
A key buzzword in 2020 is cybersecurity, but isn't it just another word for information security? The International Organization for Standardization (ISO) 27701 standard for information security specifies that BC/DR plans are in place. That's no accident. If there's truth that a cybersecurity breach or attack can severely disrupt an organization's ability to run the business, then any initiatives to respond to a cybersecurity attack must be able to trigger BC/DR plans, if needed.
While an information security or cybersecurity program is de rigueur in most IT organizations today, BC/DR plans may not be. Or perhaps they are the responsibility of another department within the firm. Either way, a cybersecurity attack has a strong likelihood of negatively impacting an organization, if not rapidly mitigated. As such, establishing linkages among cybersecurity and BC/DR plans is an important and potentially auditable activity.
IT strategic plans in 2020 and beyond
If IT strategic plans are either scheduled for updating in 2020 or are in the third or fourth year of a five-year plan, cybersecurity efforts most likely factor into those plans. But it's important to make sure that the BC/DR plans are also factored in.
Incorporate BC/DR plans and their relationships to cybersecurity plans into strategic plans, as they are likely to be more closely linked as we progress through the decade. Perhaps the most important truth to acknowledge is that the likelihood of a cybersecurity incident increases daily. Insufficient preparation could damage an organization and its reputation.
Establishing the linkages
Questions will naturally occur as an organization examines how cybersecurity and business continuity plans interact. It's no secret that BC/DR activities often occupy separate silos from cybersecurity. Those barriers need to come down and the following guidance will help achieve that goal.
Does the organization have BC/DR plans?
Implementing BC/DR plans has become vital for organizations across several industries. BC plans typically provide guidance on recovering disrupted business processes so the organization can resume normal business as quickly as possible. BC plans may also trigger DR plans to recover and restore disrupted IT infrastructure elements that enable critical business processes. These two plans can operate independently or in alignment with each other.
Ideally, according to industry good practice, a disruptive incident should trigger an IR plan that assesses the damage and initiates steps to respond quickly to the cyber incident. Results of the IR plan can trigger a BC or a DR plan, or both, based on the nature of the event. BC/DR plans recover and restore critical assets -- people, processes, technology and facilities -- the business needs to function.
Cybersecurity plans respond to specific disruptive events and may include an IR plan component to determine the nature of the event before launching response activities. The key is to determine at what point the cybersecurity attack threatens the organization and its ability to conduct business. This suggests that descriptive language should be added to cybersecurity plans to trigger IR, as well as BC/DR plans.
How do the plans interact?
Let's assume there's a full complement of plans in place that deal with business- and technology-focused incidents. In some cases, only a specific security strategy or plan -- e.g., information security -- will be needed. In other situations, one or more plans may need to be launched. The figure below depicts a simple decision flow diagram showing how such plan linkages may be arranged and launched in response to a cybersecurity attack.
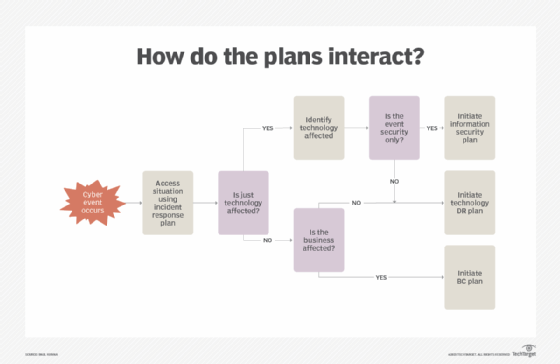
Clearly, there is no one-size-fits-all approach to the nature of cybersecurity attacks. The IR plan is a key component in the above figure as it provides the initial intelligence for making critical decisions going forward. As noted previously, launching a BC plan may also trigger a DR plan or possibly an information security plan.
The ultimate flow among these security action plans needs to be worked out during the early development stages to help prevent attacks. Exercising these plans as part of a larger overall risk assessment and cybersecurity attack response strategy will help identify additional ways for the cybersecurity and business continuity plans to interact with each other.





