
pogonici - Fotolia
How secure-by-design ITSM processes can be a business differentiator
Secure ITSM procedures are essential to digital organizations' data protection processes. They can also be a bottom line boon, says information governance expert Jeffrey Ritter.
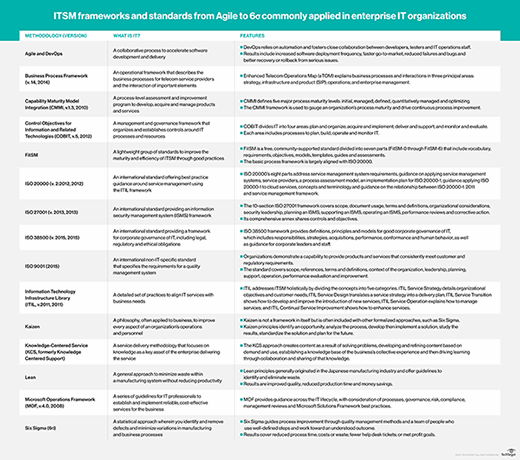
For modern companies' continued digital transformation efforts to be successful, they must embrace innovations in IT service management, according to frequent SearchCIO contributor and information governance expert Jeffrey Ritter. But as security and compliance needs continue to evolve, Ritter notes that this is having a big influence over how companies implement ITSM procedures, including putting a big onus on the ability to "trust" data generated through these processes.
In this Q&A, Ritter discusses how regulatory compliance and cybersecurity vulnerabilities are influencing ITSM implementation and how companies that build protections into ITSM processes are seeing big business benefits.
Editor's note: The following has been edited for clarity and brevity.
How has ITSM changed in the last decade or so as there has been more focus on adherence to regulatory compliance rules specific to various industries? Have compliance considerations become more of a factor when companies consider ITSM options?
Jeffrey Ritter: ITSM continues to evolve and at a more rapid pace. Yes, regulation is having an impact, and for a very important reason. Governments now realize the records of behavior inside companies are digital and they want to assure those records are, themselves, trustworthy. So, regulations are creeping into being baselines for how ITSM is to be executed. The result is that more and more of the routine business activities of ITSM now have new layers of compliance documentation to be created.
 Jeffrey Ritter
Jeffrey Ritter
While ITSM is embracing machine learning and perhaps artificial intelligence as tools for improving efficiency, professionals can never overlook asking whether the automation they are pursuing will require compliance-driven services.
If done correctly, can companies' ITSM processes actually be a business differentiator for modern, digitized companies?
Ritter: For companies to have 'modern, digitized' operations, they have to be embracing ITSM procedures and innovations. Virtually any ITSM service shares the same objective: velocity of delivery. Whatever the user-generated demand, the faster the demand is satisfied, the faster the user resumes services and reconnects to the wealth-creating goals of the business. Modern ITSM that is automated has the further advantage of achieving the same velocity objective with fewer resources or, at least, resources with a total cost of ownership that is less than the prior solutions.
Those become business differentiators because velocity accumulates. When an ITSM service is delivered faster, the user is back in business faster, the transactions or services on which the user is working move toward completion with greater velocity, and the revenue-creation outcomes of those transactions and services are realized sooner.
There are obviously business risks associated with lacking ITSM processes and procedures, but what are some of the cybersecurity and data protection risks that companies could experience without properly integrating security early on in ITSM implementation?
Ritter: The 'privacy by design' principles that have transformed how we think about privacy services are rapidly permeating into IT projects, including ITSM processes. Simply, any proposed project, whether automating existing services or improving upon whatever exists, should be designed upfront to better incorporate all of the requirements that need to be achieved. Historically, security is an enormous omission. Indeed, recently a CEO of a new startup replied to my note about the lack of security design in their product by saying that I need not be concerned because, 'Security is just a commodity we can patch on.'
Nothing is further from the truth. Any ITSM innovation in today's environment must incorporate strong design elements for security and data protection from the very beginning. Doing so helps improve the services, of course, but solid design also helps better estimate the total costs to build and operate the innovation.
Just imagine if an architect for a residential home had a wonderful design but decided not to include locks on the windows or doors. The added costs could be substantial and reduce the overall return on investment.
What types of metrics can companies incorporate to ensure ITSM procedures and processes are working properly to actually build data trust and not diminish it?
Ritter: When we are engineering trust into ITSM services, the classes of metrics to be considered are actually fairly small in number. The key metric is velocity -- a measure of time in which we measure the time taken for a designed innovation to complete the required service. Why? Time is money.
When we can calculate the economic costs of every resource involved in delivering an ITSM service based on time, the demand to achieve velocity becomes fairly compelling.
Once we calculate time, we can also add in the other key metrics: volume (how many?), efficiency (how many fails?), error correction (how many fails require added resources, such as human intervention?). Each of these helps refine our understanding of the design and performance of an innovation.
Trust is developed when the rules are being properly executed. All of these metrics are ways of measuring performance against the rules, and doing so objectively, consistently and, hopefully, on a continual basis.
There is one other metric: customer satisfaction. So many innovations are supported by the presumption that the new thing is good for the customer, but that is not always the case. Any good ITSM advocate will always design into their development and management processes steps to secure and evaluate customer satisfaction.







