shadow IT
What is shadow IT?
Shadow IT is hardware or software within an enterprise that is not supported by the organization's central IT department. Although the label itself is neutral, the term often carries a negative connotation because it implies that the IT department has not approved the technology or doesn't even know employees are using it.
Security risks from shadow IT
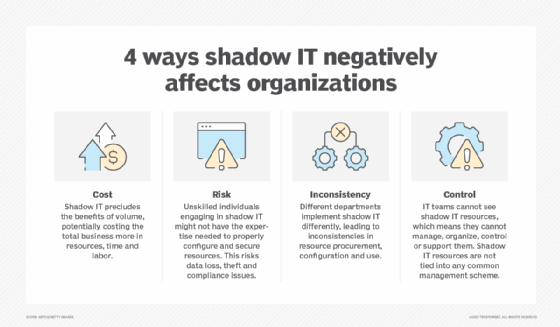
Shadow IT can introduce security risks when unsupported hardware and software are not subject to the same security measures that are applied to supported technologies. Furthermore, technologies that operate without the IT department's knowledge can negatively affect the user experience of other employees by using up network bandwidth and creating situations in which network or software application protocols conflict. Shadow IT can also become a compliance concern -- for example, when an employee stores corporate data in their personal Dropbox account.
Why employees use shadow IT
In the past, shadow IT was often the result of an impatient employee's desire for immediate access to hardware, software or a specific web service without going through the necessary steps to obtain the technology through corporate channels.
With the consumerization of IT and cloud computing, however, the meaning expands to cloud services that meet the unique needs of a particular business division and are supported by a third-party service provider or in-house group instead of by corporate IT. Popular shadow apps include Google Docs and instant messaging services such as Slack. It even includes personal technology that employees use at work, sometimes as part of a bring-your-own-device policy. Popular shadow technologies include personal smartphones, tablets and USB flash drives.
Feelings toward shadow IT are mixed. Some IT administrators fear that if shadow IT is allowed, end users will create data silos and prevent information from flowing freely throughout the organization. Other administrators believe that in a fast-changing business world, the IT department must embrace shadow IT for the innovation it supplies, and create policies for overseeing and monitoring its acceptable use.
Editor's note: This article was originally written by Caitlin White and expanded by Kathleen Casey.






