risk assessment framework (RAF)
What is a risk assessment framework and how does it work?
A risk assessment framework (RAF) is a strategy for prioritizing and sharing information about the security risks to an information technology (IT) infrastructure. A good RAF organizes and presents information in a way that both technical and non-technical personnel can understand.
RAF has the three following important components:
- shared vocabulary
- consistent assessment methods
- reporting system
Common risk assessment frameworks and techniques help an organization identify which systems are at low or high risk for abuse or attack. However, risk assessments are highly subjective, which means they cannot be relied on to consistently meet their objectives. As a result, subjectivity prevents RAFs from being used in verification audits, compliance reviews, etc.
Nevertheless, the data provided by an RAF is useful for proactively addressing potential threats, planning budgets and creating a culture in which the value of data is understood and appreciated.
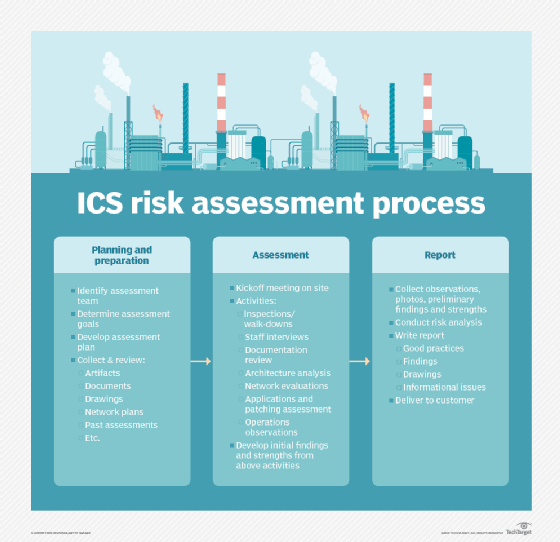
What are the different types of RAFs?
There are several risk assessment frameworks accepted as industry standards. These include the following:
- Factor Analysis of Information Risk (FAIR);
- Committee of Sponsoring Organizations of the Treadway Commission (COSO) Risk Management Framework;
- Control Objectives for Information and Related Technology (COBIT) from the Information Systems Audit and Control Association;
- Operationally Critical Threat, Asset and Vulnerability Evaluation (OCTAVE) from the Computer Emergency Readiness Team;
- Risk Management Guide for Information Technology Systems from the National Institute of Standards (NIST); and
- Threat Agent Risk Assessment (TARA).
These common risk assessment and risk management frameworks use different approaches to assess risk. For example, an information security risk assessment framework will assess IT risks like vulnerabilities, compliance, financial, operational and strategic risks.
All of these risk assessment frameworks concentrate on identifying potential risks, measuring and evaluating the impact of those potential risks, categorizing and prioritizing risks, developing an action plan to mitigate risk and documenting responses. These RAFs also demand consistent monitoring, reviews, follow-ups and governance protocols.
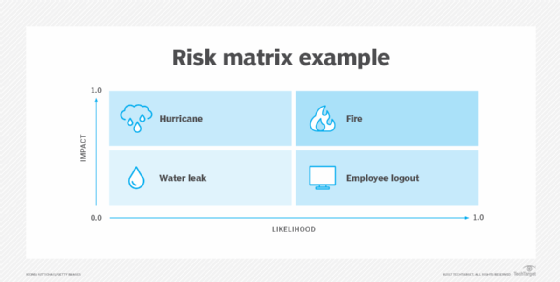
How to create a risk assessment framework
To create a risk management framework, an organization can use or modify the guides provided by NIST, OCTAVE or COBIT or create a framework that fits the organization's business requirements.
When using a risk assessment framework template, it's important to leverage a uniform numerical scale of 1 to 10, where 10 represents the most unfavorable consequence. It can also be split into a bucket of five to provide a high and a low for each bucket. For example, 1-2, 3-4, 5-6 and so on. The use of uniform scales makes it easy to do the math during the assessment process.
It also helps to provide a clear definition of what the numbers represent and reduce any ambiguity.
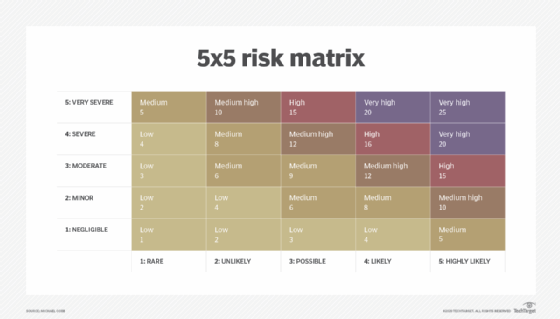
Regardless of the criteria that an organization chooses, everything must be represented on a 1–10 scale and calibrated. This approach enables the aggregation of assessments and offers a holistic view of risk. It also helps to leverage universal business elements to break down risk assessments into basic elements like processes, resources and protocols standardized across business units or silos.
However, organizations need to conduct risk assessments of vendor characteristics separately to identify and maintain objectivity. By linking different elements together, for example, connecting vendors to products and services that business processes depend on, and by linking each financial component to the business process that contributes to it, organizations can arrive at a single overall score of each process to help prioritize focus.
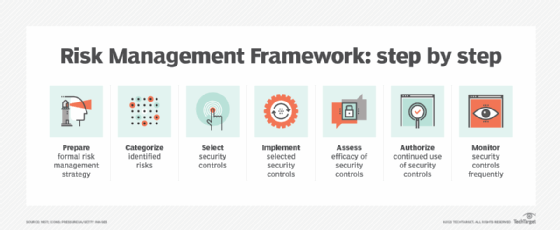
An IT risk assessment framework should have the following:
- Categorize and take inventory of all IT assets, including hardware, software, data, processes and interfaces to external systems.
- Identify threats. Natural disasters or power outages should be considered in addition to threats such as malicious access to systems or malware attacks.
- Identify corresponding vulnerabilities. Data about vulnerabilities can be obtained from security testing and system scans. Anecdotal information about known software or vendor issues should also be considered.
- Prioritize potential risks. Prioritization has three sub-phases: evaluating existing security controls, determining the likelihood and impact of a breach based on those controls and assigning risk levels.
- Document risks and determine action. This is an ongoing process with a predetermined schedule for issuing reports. The report should document the risk level for all IT assets, define what level of risk an organization is willing to tolerate and accept, and identify procedures at each risk level for implementing and maintaining security controls.
INSERT VIDEO
See also: How to perform a cybersecurity risk assessment in 5 steps, risk management vs. risk assessment vs. risk analysis, how do risk assessment costs vary and why? and best practices for data center risk assessment. Check out this free IT risk assessment template.








