risk assessment
What is a risk assessment?
Risk assessment is the process of identifying hazards that could negatively affect an organization's ability to conduct business. These assessments help identify inherent business risks and prompt measures, processes and controls to reduce the impact of these risks on business operations.
Risk assessments help ensure the health and safety of employees and customers by identifying potential hazards. The goal of this process is to determine what measures should be implemented to mitigate those risks. For example, certain hazards or risks might determine the type of protective gear and equipment a worker needs.
Different industries present different types of hazards, and as such, risk assessments vary from industry to industry.
As a risk assessment is conducted, vulnerabilities and weaknesses that could make a business more hazardous are analyzed. Potential vulnerabilities could include construction deficiencies, security issues and process system errors. Companies can use a risk assessment framework (RAF) to prioritize and share the details of the assessment, including any risks to their IT infrastructure. The RAF helps an organization identify hazards and any business assets put at risk by these hazards, as well as potential fallout if these risks come to fruition. If a hazard has a large enough impact, then a mitigation strategy can be constructed.
In large enterprises, the chief risk officer or a chief risk manager usually conducts the risk assessment process.
Risk assessments are also a major component of a risk analysis -- a similar process of identifying and analyzing potential issues that could negatively affect key business initiatives or projects.
This article is part of
What is risk management and why is it important?
Risk assessment steps
How a risk assessment is conducted varies widely, depending on the risks unique to a business's industry and the compliance rules applied to that given business or industry. However, organizations can follow these five general steps, regardless of their business type or industry.
Step 1: Identify the hazards. Identify any potential hazards that, if they were to occur, would negatively influence the organization's ability to conduct business. Potential hazards that could be considered or identified during risk assessments include natural disasters, utility outages, cyber attacks and power failure.
Step 2: Discover what or whom could be harmed. Determine which business assets would be negatively influenced if the risk came to fruition. Business assets deemed at risk of these hazards can include critical infrastructure, IT systems, business operations, company reputation and even employee safety.
Step 3: Evaluate the level of risk and develop control measures. A risk analysis can help identify how hazards will impact business assets, as well as define a risk management framework to minimize or eliminate the effect of these hazards on business assets. Other threats include property damage, business interruption, financial loss and legal penalties.
Step 4: Record the findings. The risk assessment findings should be recorded by the company and filed as easily accessible, official documents. The records should include details on potential hazards, their associated risks and plans to prevent the hazards.
Step 5: Review and update the risk assessment regularly. Potential hazards, risks and their resulting controls can change rapidly in a modern business environment. It is important for companies to update their risk assessments regularly to adapt to these changes.
Risk assessment tools and frameworks -- such as risk assessment templates -- are available for different industries. They might prove useful to companies developing their first risk assessments or for updating older ones. Some examples of these frameworks include the National Institute of Standards and Technology Cybersecurity Framework for cybersecurity purposes, ISO 27001 for IT purposes or the CSA Standard Z1002 for health and safety purposes.
How to use a risk assessment matrix
A risk assessment matrix shows the likelihood of events happening and the potential consequences. In the following example, Likelihood refers to the level of possibility that a person could be injured if exposed to a hazard, while Impact refers to the severity of the injury.
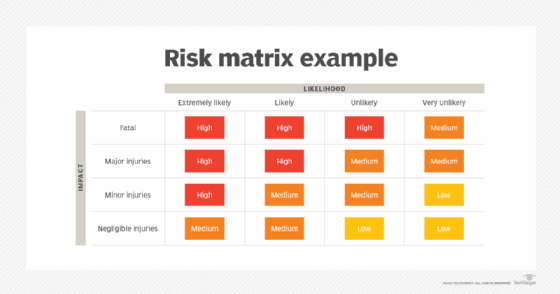
Risk matrixes can be created as 2×2, 3×3, 4×4 or 5×5 charts -- the level of detail required can help determine the size. Color coding the matrix is critical, as this represents the probability and impact of the risks that have been identified. Injury severity and consequence could be assessed as fatal, major injury, minor injury or negligible injuries. Similarly, likelihood could be assessed as extremely likely, likely, unlikely or highly unlikely.
Quantitative vs. qualitative
Risk assessments can be quantitative or qualitative. In a quantitative risk assessment, the chief risk officer or chief risk manager assigns numerical values to the probability an event will occur and the impact it would have. These numerical values can then be used to calculate an event's risk factor, which, in turn, can be mapped to a dollar amount.
Qualitative risk assessments, which are used more often, don't involve numerical probabilities or predictions of loss. The goal of a qualitative approach is to simply rank which risks pose the most danger.
While qualitative risk analysis is based on a person's judgment of risk, quantitative risk analysis is based on specific data.

The goal of risk assessments
Similar to risk assessment steps, the specific goals of risk assessments will vary based on industry, business type and relevant compliance rules. An information security risk assessment, for example, should identify gaps in the organization's IT security architecture, as well as review compliance with infosec-specific laws, mandates and regulations.
The general goal of a risk assessment is to evaluate potential hazards and remove or mitigate them.
As an example, some common goals and objectives when conducting an IT risk assessment could include the following:
- Develop a risk profile that provides a quantitative analysis of the types of threats the organization faces.
- Develop an accurate inventory of IT assets and data assets.
- Justify the cost of security countermeasures to mitigate risks and vulnerabilities.
- Develop an accurate inventory of IT assets and data assets.
- Identify, prioritize and document risks, threats and known vulnerabilities to the organization's production infrastructure and assets.
- Determine budgeting to remediate or mitigate the identified risks, threats and vulnerabilities.
- Understand the return on investment if funds are invested in infrastructure or other business assets to offset potential risk.
The ultimate goal of the risk assessment process is to evaluate hazards and determine the inherent risk created by those hazards. The assessment should not only identify hazards and their potential effects but also potential risk control measures to offset any negative impact on the organization's business processes or assets.
Examples of risk assessments by field
The components of a risk assessment differ, depending on an organization's specific industry. Typically, an assessment takes into account specific needs and provides corresponding control measures. Some examples of risk assessments include the following:
- Cybersecurity risk assessments. Team members within an organization use these to identify and prioritize risks from cyber threats associated with the organization's systems and data.
- IT risk assessments. IT or network staff use these to identify any risks facing information systems, networks and data.
- Health and safety risk assessments. Safety managers use these to identify hazards that fall under biological, chemical, energy and environmental risks that apply to a workplace or job.
- Workplace risk assessments. Both office and school administrators use these to ensure a workplace is free from health and safety hazards.
- Project management risk assessments. Project managers and team members use these to identify potential risks, hazards and impacts that a project faces.
- Environmental risk assessments. Risk assessors and organizations such as the U.S. Environmental Protection Agency use these to assess any human or ecological health risks associated with exposure to possible environmental contaminants. This type of assessment determines an acceptable level of contaminants that can remain in a location while still remaining nonthreatening to public health.
- Climate risk assessments. Organizations and climate risk analysts use these to assess the potential of climate-related events and trends that could cause damage and loss, such as high or low temperatures, precipitation and hurricanes.
Learn more about how risk assessment differs from risk management and risk analysis.







